This page lists announcements of security fixes made in Critical Patch Update Advisories, Security Alerts and Bulletins, and it is updated when new Critical Patch Update Advisories, Security Alerts and Bulletins are released.
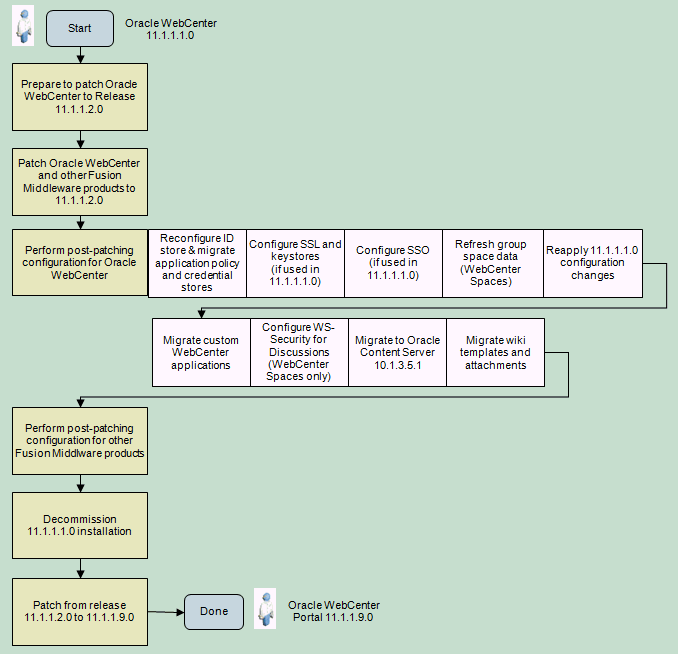
Download and Extract the Installation Software Shut Down Oracle Databases Shut down any existing Oracle database instances with normal or immediate priority Stop All Processes Stop all listener and other processes running in the Oracle home directory where you want to install the patch set. In this article, we will explain the steps for applying patch Database Jan 2018 Release Update (DB RU) on oracle 12.2 database. Beginning in July 2017, Oracle has transitioned to a more flexible and responsive strategy for the database software release process. Step by Step to apply patches in Oracle Apps R12.2. By using adop utility Hi DBA-Mates, As we are knowing that applying patch in ORACLE EBS R12.2 is different than R12.1. Steps to apply a patch: - Stop all application services (keep the database and the database listener up and running) - Download the patch from Metalink - Copy the patch file to any directory (i.e. /u04/patches) - As 'applmgr' do the following: - Source the environment file - $ cd /u04/patches - Type 'unzip patchnumber.zip' - cd patchnumber - Type 'adpatch' - When it prompts you to enter. The patch you have downloaded has been saved to a directory that is named for the patch number in My Oracle Support. In this case, the patch number is 15941858. The user changes directory to the patch directory and then runs the OPatch apply command.
Instructions for subscribing to email notifications of Critical Patch Update Advisories and Security Alerts.
Oracle Corporate Security Blog
Guidelines for reporting security vulnerabilities
This page contains the following sections:
Critical Patch Updates
Critical Patch Updates are collections of security fixes for Oracle products. They are available to customers with valid support contracts. They are released on the Tuesday closest to the 17th day of January, April, July and October. The next four dates are:
- 15 October 2019
- 14 January 2020
- 14 April 2020
- 14 July 2020
A pre-release announcement will be published on the Thursday preceding each Critical Patch Update release.
The Critical Patch Updates released since 2015 are listed in the following table. Critical Patch Updates released before 2015 are available here.
| Critical Patch Update | Latest Version/Date |
|---|---|
| Critical Patch Update - July 2019 | Rev 5, 16 August 2019 |
| Critical Patch Update - April 2019 | Rev 6, 28 May 2019 |
| Critical Patch Update - January 2019 | Rev 6, 18 April 2019 |
| Critical Patch Update - October 2018 | Rev 6, 18 December 2018 |
| Critical Patch Update - July 2018 | Rev 8, 12 October 2018 |
| Critical Patch Update - April 2018 | Rev 4, 10 December 2018 |
| Critical Patch Update - January 2018 | Rev 8, 20 March 2018 |
| Critical Patch Update - October 2017 | Rev 10, 15 February 2018 |
| Critical Patch Update - July 2017 | Rev 6, 20 March 2018 |
| Critical Patch Update - April 2017 | Rev 5, 20 June 2017 |
| Critical Patch Update - January 2017 | Rev 5, 18 May 2017 |
| Critical Patch Update - October 2016 | Rev 5, 16 May 2019 |
| Critical Patch Update - July 2016 | Rev 2, 18 October 2016 |
| Critical Patch Update - April 2016 | Rev 3, 20 December 2016 |
| Critical Patch Update - January 2016 | Rev 2, 12 February 2016 |
| Critical Patch Update - October 2015 | Rev 6, 27 October 2015 |
| Critical Patch Update - July 2015 | Rev 4, 30 July 2015 |
| Critical Patch Update - April 2015 | Rev 3, 28 April 2015 |
| Critical Patch Update - January 2015 | Rev 2, 10 March 2015 |
Security Alerts
Oracle will issue Security Alerts for vulnerability fixes deemed too critical to wait for distribution in the next Critical Patch Update. The Security Alerts released since 2015 are listed in the following table. Security Alerts released before 2015 are available here.
| Security Alert Number And Description | Latest Version/Date |
|---|---|
| Alert for CVE-2019-2729 | Rev 4, 11 July 2019 |
| Alert for CVE-2019-2725 | Rev 4, 29 May 2019 |
| Alert for CVE-2018-11776 | Rev 1, 31 August 2018 |
| Alert for CVE-2018-3110 | Rev 1, 10 August 2018 |
| Alert for CVE-2017-10269 | Rev 2, 16 November 2017 |
| Alert for CVE-2017-10151 | Rev 3, 04 November 2017 |
| Alert for CVE-2017-9805 | Rev 1, 22 September 2017 |
| Alert for CVE-2017-3629 | Rev 2, 20 June 2017 |
| Alert for CVE-2016-0636 | Rev 1, 23 March 2016 |
| Alert for CVE-2016-0603 | Rev 1, 05 February 2016 |
| Alert for CVE-2015-4852 | Rev 2, 12 November 2015 |
| Alert for CVE-2015-3456 QEMU 'Venom' | Rev 1, 15 May 2015 |
Solaris Third Party Bulletins
Solaris Third Party Bulletins are used to announce security fixes for third party software distributed with Oracle Solaris. Solaris Third Party Bulletins are published on the same day as Oracle Critical Patch Updates are released. These bulletins are be updated on the Tuesday closest to the 17th of the following two months after their release (i.e., the two months between the normal quarterly Critical Patch Update publication dates). In addition, Solaris Third Party Bulletins may also be updated for vulnerability fixes deemed too critical to wait for the next scheduled publication date. Bulletins published before January 20, 2015 are available here.
| Solaris Third Party Bulletin | Latest Version/Date |
|---|---|
| Solaris Third Party Bulletin - July 2019 | Rev 3, 17 September 2019 |
| Solaris Third Party Bulletin - April 2019 | Rev 3, 25 June 2019 |
| Solaris Third Party Bulletin - January 2019 | Rev 4, 16 April 2019 |
| Solaris Third Party Bulletin - October 2018 | Rev 3, 14 December 2018 |
| Solaris Third Party Bulletin - July 2018 | Rev 3, 24 September 2018 |
| Solaris Third Party Bulletin - April 2018 | Rev 3, 15 June 2018 |
| Solaris Third Party Bulletin - January 2018 | Rev 3, 20 March 2018 |
| Solaris Third Party Bulletin - October 2017 | Rev 3, 18 December 2017 |
| Solaris Third Party Bulletin - July 2017 | Rev 4, 18 September 2017 |
| Solaris Third Party Bulletin - April 2017 | Rev 4, 19 June 2017 |
| Solaris Third Party Bulletin - January 2017 | Rev 4, 28 March 2017 |
| Solaris Third Party Bulletin - October 2016 | Rev 5, 11 January 2017 |
| Solaris Third Party Bulletin - July 2016 | Rev 6, 10 April 2017 |
| Solaris Third Party Bulletin - April 2016 | Rev 8, 16 October 2017 |
| Solaris Third Party Bulletin - January 2016 | Rev 5, 12 April 2016 |
| Solaris Third Party Bulletin - October 2015 | Rev 5, 14 January 2016 |
| Solaris Third Party Bulletin - July 2015 | Rev 6, 15 September 2015 |
| Solaris Third Party Bulletin - April 2015 | Rev 3, 15 June 2015 |
| Solaris Third Party Bulletin - January 2015 | Rev 5, 01 April 2015 |
Oracle Linux Bulletins
Oracle releases security advisories for Oracle Linux as patches become available. Security advisories (ELSA) are published at https://linux.oracle.com/security/.
Starting October 20, 2015, Oracle will also publish Oracle Linux Bulletins which list all CVEs that had been resolved and announced in Oracle Linux Security Advisories in the last one month prior to the release of the bulletin. The Oracle Linux Bulletin will be published on the same day as Oracle Critical Patch Updates are released. These bulletins will also be updated for following two months after their release (i.e., the two months between the normal quarterly Critical Patch Update publication dates) to cover all CVEs that had been resolved in those two months following the bulletin's publication. In addition, Oracle Linux Bulletins may also be updated for vulnerability fixes deemed too critical to wait for the next scheduled bulletin publication date.
How To Apply Patch Oracle Database
| Oracle Linux Bulletin | Latest Version/Date |
|---|---|
| Oracle Linux Bulletin - July 2019 | Rev 3, 19 September 2019 |
| Oracle Linux Bulletin - April 2019 | Rev 3, 18 June 2019 |
| Oracle Linux Bulletin - January 2019 | Rev 3, 18 March 2019 |
| Oracle Linux Bulletin - October 2018 | Rev 3, 17 December 2018 |
| Oracle Linux Bulletin - July 2018 | Rev 3, 18 September 2018 |
| Oracle Linux Bulletin - April 2018 | Rev 3, 18 June 2018 |
| Oracle Linux Bulletin - January 2018 | Rev 3, 16 March 2018 |
| Oracle Linux Bulletin - October 2017 | Rev 3, 18 December 2017 |
| Oracle Linux Bulletin - July 2017 | Rev 3, 18 September 2017 |
| Oracle Linux Bulletin - April 2017 | Rev 3, 19 June 2017 |
| Oracle Linux Bulletin - January 2017 | Rev 3, 17 March 2017 |
| Oracle Linux Bulletin - October 2016 | Rev 3, 19 December 2016 |
| Oracle Linux Bulletin - July 2016 | Rev 3, 19 September 2016 |
| Oracle Linux Bulletin - April 2016 | Rev 3, 20 June 2016 |
| Oracle Linux Bulletin - January 2016 | Rev 3, 21 March 2016 |
| Oracle Linux Bulletin - October 2015 | Rev 3, 21 December 2015 |
Oracle VM Server for x86 Bulletins
Oracle releases security advisories for Oracle VM Server for x86 as patches become available. Security advisories (OVMSA) are published at https://linux.oracle.com/errata/.
Starting July 19, 2016, Oracle will also publish Oracle VM Server for x86 Bulletins which will list all CVEs that had been resolved and announced in Oracle VM Server for x86 Security Advisories in the last one month prior to the release of the bulletin. The Oracle VM Server for x86 Bulletin will be published on the same day as Oracle Critical Patch Updates are released. These bulletins will also be updated for following two months after their release (i.e., the two months between the normal quarterly Critical Patch Update publication dates) to cover all CVEs that had been resolved in those two months following the bulletin's publication. In addition, Oracle VM Server for x86 Bulletins may also be updated for vulnerability fixes deemed too critical to wait for the next scheduled bulletin publication date.
| Oracle VM Server for x86 Bulletin | Latest Version/Date |
|---|---|
| Oracle VM Server for x86 Bulletin - July 2019 | Rev 2, 16 August 2019 |
| Oracle VM Server for x86 Bulletin - April 2019 | Rev 3, 18 June 2019 |
| Oracle VM Server for x86 Bulletin - January 2019 | Rev 3, 18 March 2019 |
| Oracle VM Server for x86 Bulletin - October 2018 | Rev 3, 17 December 2018 |
| Oracle VM Server for x86 Bulletin - July 2018 | Rev 3, 18 September 2018 |
| Oracle VM Server for x86 Bulletin - April 2018 | Rev 3, 18 June 2018 |
| Oracle VM Server for x86 Bulletin - January 2018 | Rev 3, 16 March 2018 |
| Oracle VM Server for x86 Bulletin - October 2017 | Rev 3, 18 December 2017 |
| Oracle VM Server for x86 Bulletin - July 2017 | Rev 3, 18 September 2017 |
| Oracle VM Server for x86 Bulletin - April 2017 | Rev 3, 19 June 2017 |
| Oracle VM Server for x86 Bulletin - January 2017 | Rev 3, 17 March 2017 |
| Oracle VM Server for x86 Bulletin - October 2016 | Rev 3, 19 December 2016 |
| Oracle VM Server for x86 Bulletin - July 2016 | Rev 3, 19 September 2016 |

Map of CVE to Advisory
The Map of CVE to Advisory/Alert indicates which CVEs are fixed in each Critical Patch Update and Security Alert. The Map of CVE to Solaris Third Party Bulletin indicates which CVEs are fixed in each Solaris Third Party Bulletin.
Policy on Information Provided in Critical Patch Updates and Security Alerts
As a matter of policy, Oracle will not provide additional information about the specifics of vulnerabilities beyond what is provided in the Critical Patch Update or Security Alert notification, the pre-installation notes, the readme files, and FAQs. Oracle provides all customers with the same information in order to protect all customers equally. Oracle will not provide advance notification or 'insider information' on Critical Patch Update or Security Alerts to individual customers. Finally, Oracle does not develop or distribute active exploit code (or 'proof of concept code') for vulnerabilities in our products.
Applicability of Critical Patch Updates and Security Alerts to Oracle Cloud
The Oracle Cloud operations and security teams regularly evaluate Oracle’s Critical Patch Updates and Security Alert fixes as well as relevant third-party fixes as they become available and apply the relevant patches in accordance with applicable change management processes.
Customers requiring additional information that is not addressed in the Critical Patch Update Advisory may obtain additional information as follows:
Oracle How To Apply Jdk Patch
- Oracle Cloud (IaaS, PaaS, and SaaS) customers should submit a SR within their designated support system
- Oracle Managed Cloud Services (OMCS) customers should contact their Service Delivery Manager (SDM). CRM On Demand customers should request status via a Service Request (SR).
- Global Business Units/Industry Cloud Services and Micros Cloud customers should submit a SR within their designated support system or, if applicable, contact their Customer Success Manager.
- Oracle Data Cloud (ODC) customers should contact their Client Partner.
- Oracle NetSuite customers should submit an Oracle NetSuite Support Case from within their Oracle NetSuite account.